SQL (Structured Query Language) is a language for interaction with the database . SQL injection is a web application attack to inject malicious syntax in SQL Queries .
BLIND SQL INJECTION
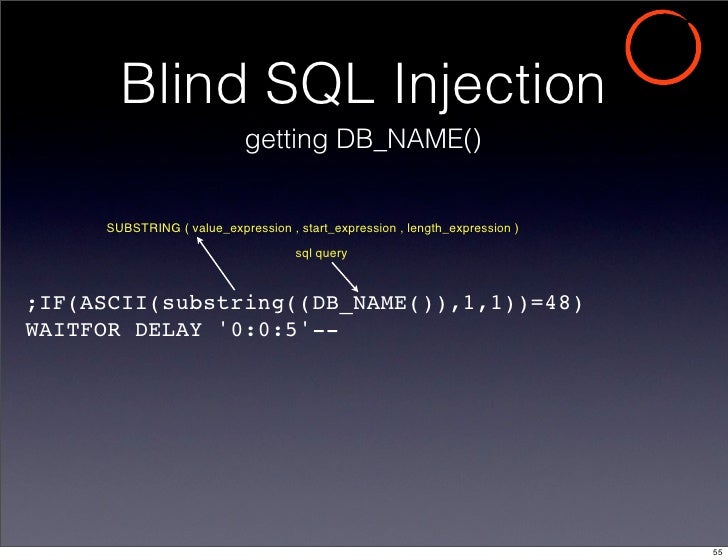
Blind SQL Injection consists of techniques for exploiting the SQL injection vulnerabilities by performing a Binary search by putting one character at a time. Well this is very time consuming .
An Example of Blind SQL injection is :
Blind SQL Injection Case:
QUERY evaluates to:
Well we have a lot of tools that can be used for penetration testing for Blind SQL injection :
- SQLMAP
- SQLNINJA
- BSQL Hacker
- Mole
- Havij …… etc …..
Though during penetration testing , if these tools dont work , mostly we end up writing a custom script . So here is a treat !! BBSQL can simplify tricky blind SQL injection attack .
Blind SQL Injection with BBQSQL
BBSQL can be used to exploit the Blind SQL injection and can help to reach for hidden vulnerabilities .
BBSQL is fast , simple , versatile and extensible .
BBQSQL is a blind SQL injection framework written in Python. It is extremely useful when attacking tricky SQL injection vulnerabilities. BBQSQL is also a semi-automatic tool, allowing quite a bit of customization for those hard to trigger SQL injection findings.
The tool is built to be database agnostic and is extremely versatile. It also has an intuitive UI to make setting up attacks much easier. Python gevent is also implemented, making BBQSQL extremely fast.
Similar to other SQL injection tools you provide certain request information.
Must provide the usual information:
- URL
- HTTP Method
- Headers
- Cookies
- Encoding methods
- Redirect behavior
- Files
- HTTP Auth
- Proxies
Here is a Usage guide for the Tool :
Happy hunting !!! Blind SQL is now simple and Fast .
# This tools is really Fast . Try it !! comes built in Kali Linux !!
#For educational purpose only , Penetration testing without permission is legal offence . The Author holds no responsibility if you misuse this tutorial .

No comments :
Post a Comment